
SOCRadar Announces $5M Series A Funding for New Extended Threat Intell...
SOCRadar Announces $5M Series A Funding for New Extended Threat Intelligence (XTI) Cybersecurity Platform Funding will support the expansion of SOCRadar’s single-platform early warning system that off...
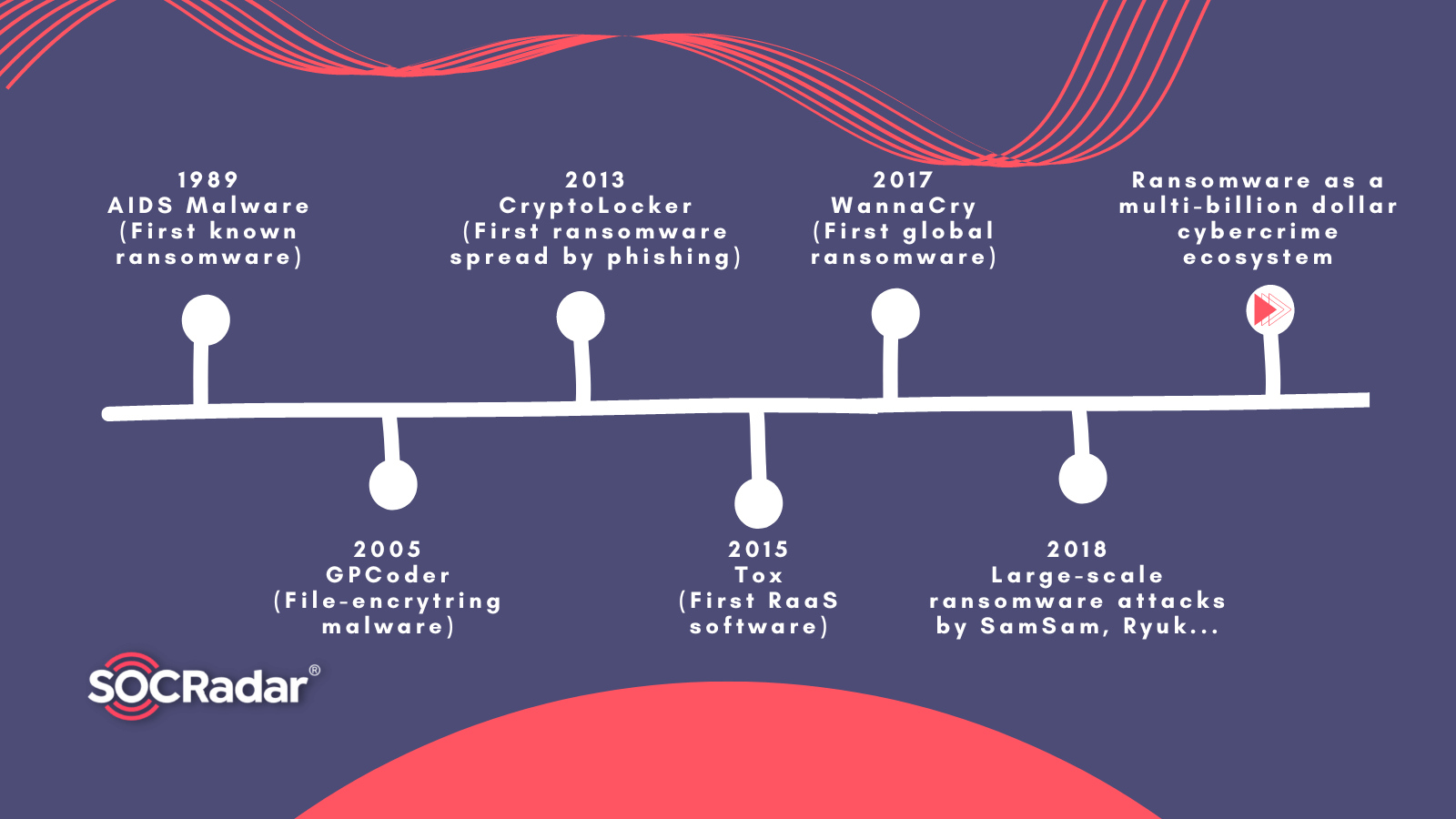
Evolution of Ransomware: So Far and Hereafter
Evolution of Ransomware: So Far and Hereafter By SOCRadar Research Ransomware attacks have become a potential threat to all enterprises, regardless of industry or size. Ransomware can target any indiv...

Critical Unauthenticated RCE Vulnerability in Fortinet Products: CVE-2...
Critical Unauthenticated RCE Vulnerability in Fortinet Products: CVE-2023-25610 Fortinet has revealed a critical severity vulnerability, tracked as CVE-2023-25610, in a new advisory. It is a buff...

Major Cyberattacks in Review: February 2023
Major Cyberattacks in Review: February 2023 As we enter March 2023, the world continues to face a surge in cyberattacks that threaten individuals, businesses, and government agencies. The last month h...

How to Protect Yourself from Cyber Attacks During Tax Season?
How to Protect Yourself from Cyber Attacks During Tax Season? Not many sane persons in the US will go against the (Internal Revenue Service) IRS. Even some crazies like Batman’s supervillain Jok...

SOCRadar is the Gold Winner of Three Cybersecurity Excellence Awards
SOCRadar is the Gold Winner of Three Cybersecurity Excellence Awards We are thrilled to announce that SOCRadar, a leading provider of cyber threat intelligence solutions, has been awarded in three cat...

PoC Available for Critical RCE Vulnerability in Microsoft Word (CVE-20...
PoC Available for Critical RCE Vulnerability in Microsoft Word (CVE-2023-21716) CVE-2023-21716 was discovered in Microsoft Word last year. It is a critical remote code execution (RCE) vulnerability in...
Dark Web Profile: NoName057(16)
Dark Web Profile: NoName057(16) By SOCRadar Research [Update] July 11, 2023: NoName recently launched a cyber attack on Poland, targeting critical infrastructures such as the National Bank of Poland a...

BidenCash Leaked 2.1 Million Credit Card Information
BidenCash Leaked 2.1 Million Credit Card Information Powered by DarkMirror™ Credit card theft and the sale of credit card information are among the biggest revenue streams for threat actors on the dar...

How to Stop a DDoS Attack? (2023 Edition)
How to Stop a DDoS Attack? (2023 Edition) ...

Educational Institutions Face 234% Increase in Ransomware Attacks
Educational Institutions Face 234% Increase in Ransomware Attacks As the world becomes increasingly digital, educational institutions face a growing cyberattack threat. In 2022, cybersecurity research...

Aruba Networks Fixes Six Critical RCE Vulnerabilities Affecting ArubaO...
Aruba Networks Fixes Six Critical RCE Vulnerabilities Affecting ArubaOS In a recent security advisory, Aruba Networks disclosed thirty-three vulnerabilities. Six of them were rated as critical. The vu...

Growing Cybercrime Outsourcing Model: Initial Access Brokers
Growing Cybercrime Outsourcing Model: Initial Access Brokers By SOCRadar Research The initial access market has shown a dramatic increase in 2022 compared to the previous year. While SOCRadar observed...

Security Misconfigurations Caused 35% of All Time Cyber Incidents
Security Misconfigurations Caused 35% of All Time Cyber Incidents By SOCRadar Research Security misconfiguration is the vulnerability that arises when systems or applications are not configured proper...

The Week in Dark Web – February 27, 2023 – Access Sales and Data Leaks...
The Week in Dark Web – February 27, 2023 – Access Sales and Data Leaks Powered by DarkMirror™ The most sophisticated attacks can be based on data put up for sale on the dark web by threat actors. A pi...

Fix Available for Double Free Vulnerability in OpenSSH 9.1 (CVE-2023-2...
Fix Available for Double Free Vulnerability in OpenSSH 9.1 (CVE-2023-25136) CVE-2023-25136, a pre-authentication double-free vulnerability, has been fixed in OpenSSH version 9.2p1. The vulnerabil...

Education Threat Landscape Report: Threat Posts 61% Increased
Education Threat Landscape Report: Threat Posts 61% Increased The education industry is experiencing a digital transformation process as technology becomes more prevalent in the world. This shift is p...

An Analysis of Emerging Fortinet Vulnerabilities Trend
An Analysis of Emerging Fortinet Vulnerabilities Trend By SOCRadar Research Fortinet is one of the major cybersecurity companies and offers 56 cybersecurity products. But, such a wide range of product...

VMware Fixes Critical Vulnerability in Carbon Black App Control (CVE-2...
VMware Fixes Critical Vulnerability in Carbon Black App Control (CVE-2023-20858) VMware has recently rolled out a patch to address a critical vulnerability in its Carbon Black App Control product, whi...

The Week in Dark Web – February 20, 2023 – Access Sales and Data Leaks...
The Week in Dark Web – February 20, 2023 – Access Sales and Data Leaks Powered by DarkMirror™ Organizations’ worst nightmares are “data breaches” and “data leaks.” Atlass...

































