
The Week in Dark Web - 4 October 2021 - Ransomware Attacks and Data Le...
The Week in Dark Web – 4 October 2021 – Ransomware Attacks and Data Leaks Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. New Ransomware atta...
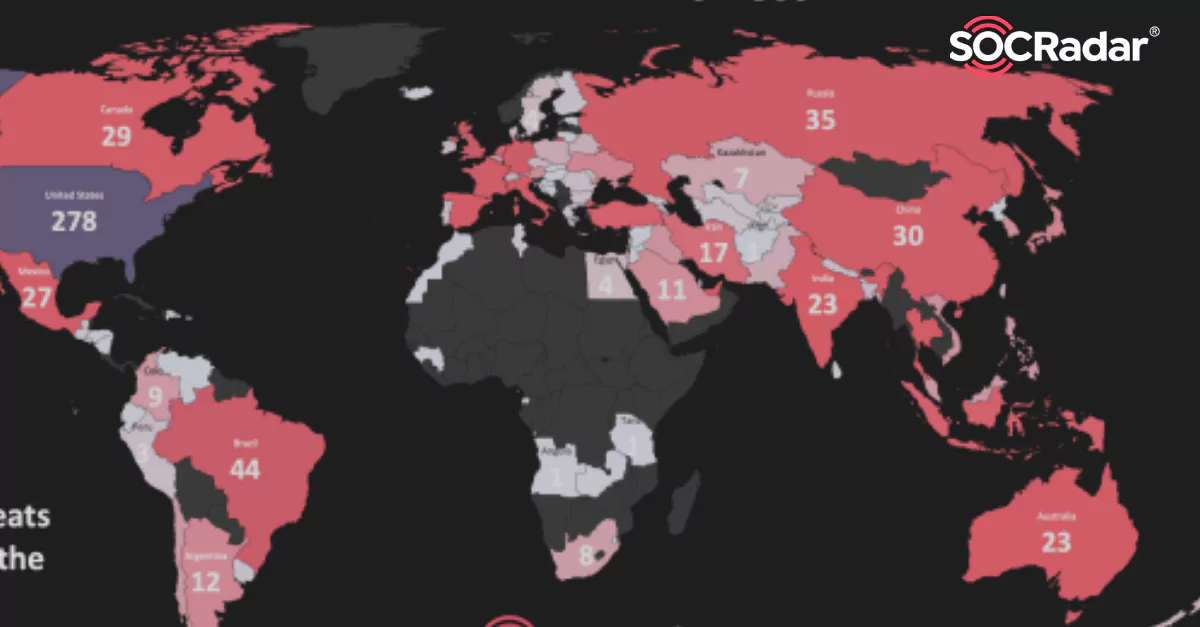
“Data Sales” is in the Lead at the Global Threat Landscape
“Data Sales” is in the Lead at the Global Threat Landscape The Global Regional DeepWeb Report, which emerged with the research of the SOCRadar analyst team, is now available for the first time. ...

Why You Should Care About Ransomware
Why You Should Care About Ransomware With a statement from FBI officials on August 25, it was said that a newly formed ransomware group “Hive” is attacking the health system in the USA. Th...

What is RedLine Stealer and What Can You Do About it?
What is RedLine Stealer and What Can You Do About it? RedLine Stealer (a.k.a. RedLine) is malicious software that can be bought from $150 – $200 depending on the version on hacker forums. RedLine can ...

What is Cybersquatting and How to Prevent it?
What is Cybersquatting and How to Prevent it? Cybersquatting (also known as domain squatting or typosquatting) is a specific type of cybercrime covered. In the US, the Anti-CybersQuatting Consumer Pro...

The Week in Dark Web - 27 September 2021 - Rise of Ransomware Attacks
The Week in Dark Web – 27 September 2021 – Rise of Ransomware Attacks Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. New Ransomware attacks,...

How to Prevent Attacks by APT Groups Using SOCRadar
How to Prevent Attacks by APT Groups Using SOCRadar ...

The Most Common Phishing Method Used by Cyber Scammers on WhatsApp
The Most Common Phishing Method Used by Cyber Scammers on WhatsApp WhatsApp is the most downloaded and used messaging application by users in the world. For this reason, cyberattacks on WhatsApp can r...

Dark Web Threat Profile: Conti Ransomware Group
Dark Web Threat Profile: Conti Ransomware Group ...

What is Tactical Cyber Threat Intelligence and How to Use it
What is Tactical Cyber Threat Intelligence and How to Use it As cyber threats become more complex than ever, many organizations devote more resources to their security programs. Almost every organizat...

The Week in Dark Web - 20 September 2021 - Cybercrime Business Evolves
The Week in Dark Web – 20 September 2021 – Cybercrime Business Evolves Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, com...

How to Detect Phishing Attacks?
How to Detect Phishing Attacks? ...

Top 5 Cyberspace Search Engines Used by Security Researchers
Top 5 Cyberspace Search Engines Used by Security Researchers We are all familiar with the concept of internet search engines such as Google, Bing, Safari, and even Yahoo. But what if you looking for i...

The Week in Dark Web - 13 September 2021 - A Mix of Cyber Attacks
The Week in Dark Web – 13 September 2021 – A Mix of Cyber Attacks Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, company ...

CISA Alert: Ransomware Gangs Take Advantage of Holidays
CISA Alert: Ransomware Gangs Take Advantage of Holidays It’s not hard to say that many security teams worldwide are understaffed and overworked. On August 31, 2021, The FBI and the CISA released an a...

How to Use SOCMINT for Better Cause?
How to Use SOCMINT for Better Cause? With the increasing use of social media by private and public practitioners, advanced methods of collecting and analyzing social media data, known as Social Media ...

How to Detect BEC Attacks?
How to Detect BEC Attacks? ...

The Week in Dark Web - 30 August 2021 - The Rise of Cybercrime in Asia
The Week in Dark Web – 30 August 2021 – The Rise of Cybercrime in Asia Powered by DarkMirror™ This week’s edition covers the latest dark web news from the past week. admin access sale, com...

How to Detect Domain Hijacking Attacks?
How to Detect Domain Hijacking Attacks? ...

Detecting IoT Devices For Your Company
Detecting IoT Devices For Your Company From smart wearables to interconnected industrial devices the IOT is becoming a larger part of our lives since the first coinage of the term in 1999 at a P&G...

































