
What is EMOTET Malware and How to Protect Yourself
What is EMOTET Malware and How to Protect Yourself According to Arne Schoenbohm, who leads the German Federal Office of Information Security (BSI), EMOTET is the king of malware. EMOTET actively attac...

Threat-Informed Defense (TID): A Threat Intelligence Perspective
Threat-Informed Defense (TID): A Threat Intelligence Perspective Cyberattacks are increasing in frequency worldwide, posing significant challenges for organizations as they strive to protect their cyb...

A Snapshot of 2023 CWE Top 25 Most Dangerous Software Weaknesses
A Snapshot of 2023 CWE Top 25 Most Dangerous Software Weaknesses Figure 1: Top 25 CWE logo (MITRE) The 2023 CWE Top 25 Most Dangerous Software Weaknesses is a list that ranks the most widespread and c...

The added OWASP Top 10 for LLMs: An Overview of Critical AI Vulnerabil...
The added OWASP Top 10 for LLMs: An Overview of Critical AI Vulnerabilities with SOCRadar Large Language Models (LLMs) are artificial intelligence models that generate human-like text. They have becom...

Top 10 Malware Analysis Platforms & Tools
Top 10 Malware Analysis Platforms & Tools While cyberspace constantly expands, some dangers like malware come to the surface in parallel. A mail attachment, an innocent-looking application downloa...

Navigating the Assets Discovery Journey with SOCRadar XTI EASM
Navigating the Assets Discovery Journey with SOCRadar XTI EASM The attack surface is the sum of all potential entry points an attacker can use to gain unauthorized access to an organization’s as...

Best of Both Worlds: CISA’s Known Exploited Vulnerabilities Integratio...
Best of Both Worlds: CISA’s Known Exploited Vulnerabilities Integration with SOCRadar External Attack Surface Management In today’s digital landscape, the threat of cyberattacks looms large, with thre...

Using OSINT to Strengthen Organizational Security
Using OSINT to Strengthen Organizational Security Open-source intelligence or “OSINT” is collecting and analyzing data gathered from publicly available open sources (social media, news, dark web, etc....

ChatGPT for SOC Analysts
ChatGPT for SOC Analysts ChatGPT, the language model developed by OpenAI, has taken the tech world by storm since its launch in November 2022. In a matter of months, it has amassed over 100 million mo...

ChatGPT for CTI Professionals
ChatGPT for CTI Professionals In 1950, Alan Turing, the father of modern computing, asked, “Can machines think?” Over the years, that question has evolved into a quest for inventing machines that can ...

What Is Cyber Threat Intelligence?
What Is Cyber Threat Intelligence? The swift adoption of information technology has coincided with an alarming surge in cyber-attacks, as malicious actors deploy increasingly sophisticated exploits. T...
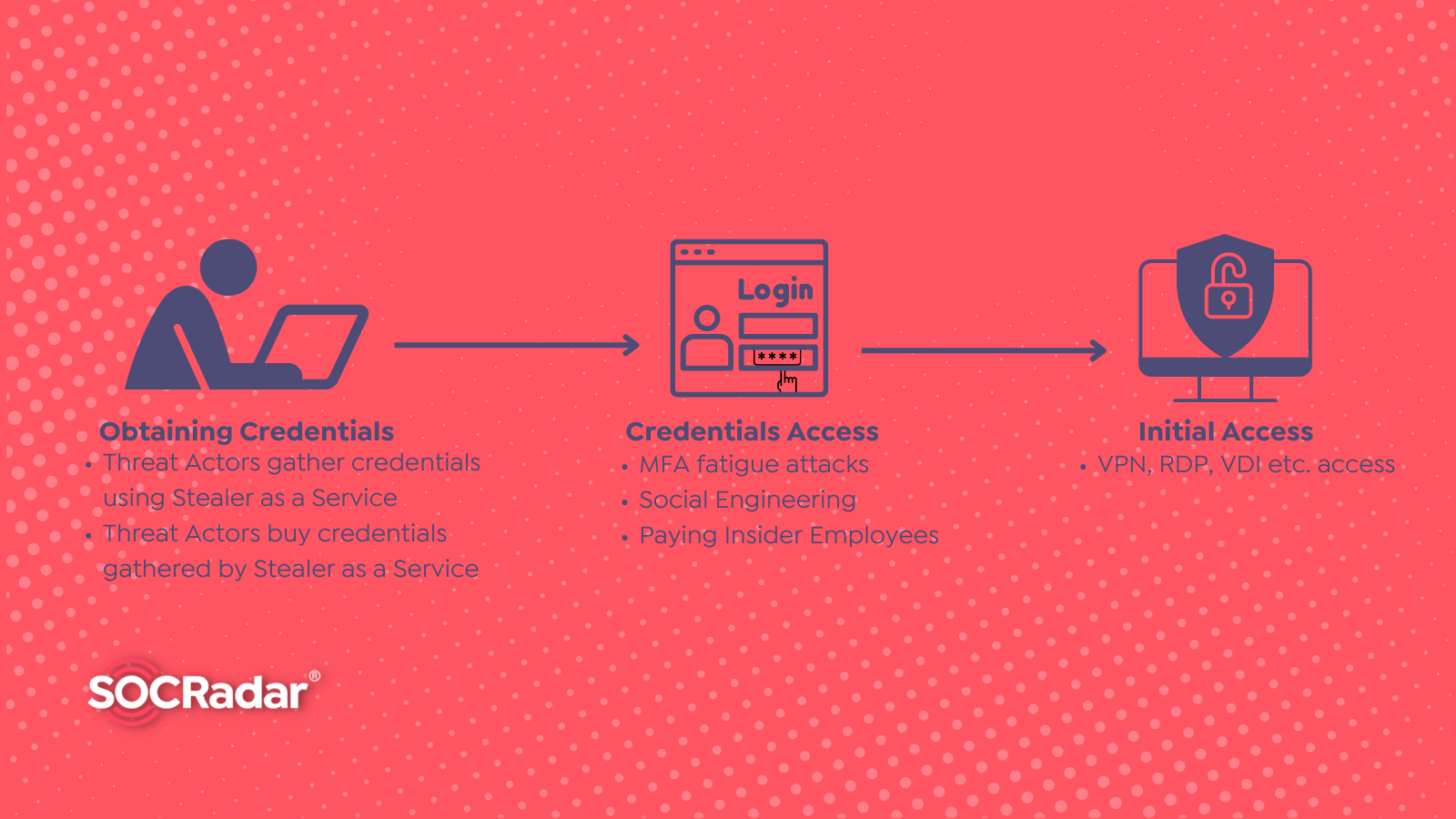
What is Stealer as a Service?
What is Stealer as a Service? By SOCRadar Research Stealer as a service is a marketing approach in which threat actors offer to sell or lease access to information-stealer tools designed to steal...

From Zero to Adversary: APTs
From Zero to Adversary: APTs By SOCRadar Research From time to time, news hit the front pages regarding cyberattacks on significant infrastructures, such as nuclear facilities, or major companies, suc...
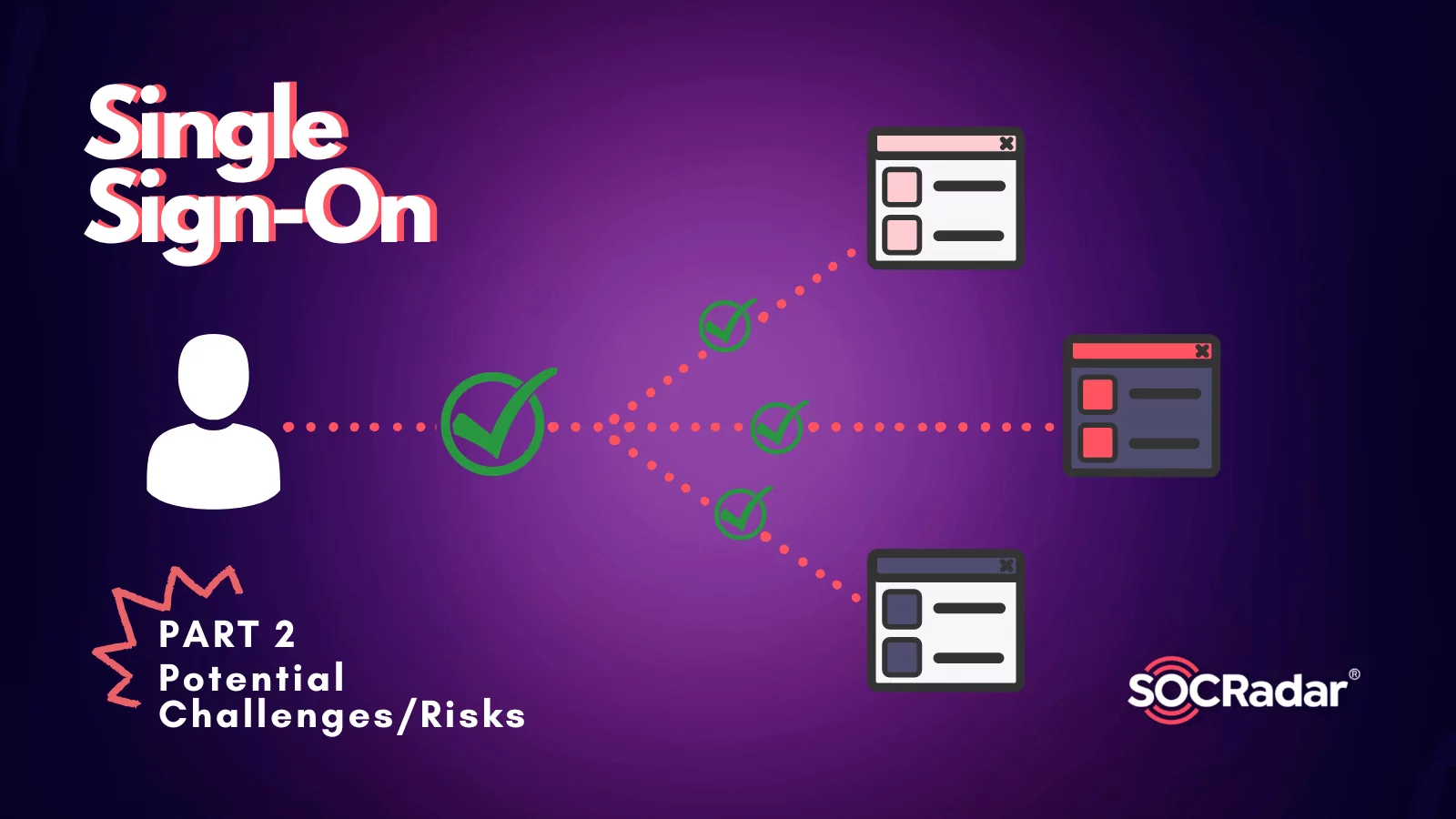
What is the Role of Single Sign-On in Security Measures? – Part 2
What is the Role of Single Sign-On in Security Measures? – Part 2 By SOCRadar Research Read the previous article: What is the Role of Single Sign-On in Security Measures? – Part 1 Maintaining easy and...

What is the Role of Single Sign-On in Security Measures? – Part 1
What is the Role of Single Sign-On in Security Measures? – Part 1 By SOCRadar Research Identity and Access Management (IAM) can be challenging in an enterprise environment. For users and administ...

Building Cybersecurity Awareness for Organizations
Building Cybersecurity Awareness for Organizations Cybersecurity has become a vital phenomenon for every institution today, but ensuring safety is a long process that includes different layers, and on...

The Ultimate OSINT Handbook on Personal Information
The Ultimate OSINT Handbook on Personal Information OSINT is a term that refers to the process of gathering information from publically accessible sources. These sources include but are not limited to...

Halloween Special: The Spookiest Cybersecurity Stories
Halloween Special: The Spookiest Cybersecurity Stories It’s the season of ghouls, ghosts, and outrageous costumes. But for cybersecurity professionals, Halloween is more likely to be a notification wa...

What are the Different Methods of Threat Detection?
What are the Different Methods of Threat Detection? Threat detection is known as the process of evaluating a security ecosystem from top to bottom to find any malicious behavior that might compromise ...

Ten Things Will Change Cybersecurity in 2023
Ten Things Will Change Cybersecurity in 2023 Businesses come across more significant cybersecurity challenges as technology evolves. The digital environment and the attack surface are changing every s...































