
Detecting Leaked Credentials with Identity & Access Intelligence
Detecting Leaked Credentials with Identity & Access Intelligence Stealers are malicious software engineered by threat actors to compromise systems. Comparable to burglars, these trojans covertly e...

Third-Party Vendor Breaches: Causes, Key Statistics, Recent Incidents,...
Third-Party Vendor Breaches: Causes, Key Statistics, Recent Incidents, and Effective Mitigation Strategies In modern business operations, most organizations extend their activities beyond their immedi...

Beyond Phishing: Top 10 Data Breach Sets
Beyond Phishing: Top 10 Data Breach Sets In recent years, there has been a significant increase in the amount of sensitive data available, making cybercrime more of a risk even for people who aren’t v...

In the Crosshairs: Top 10 Threat Actors Targeting the USA
In the Crosshairs: Top 10 Threat Actors Targeting the USA As the digital landscape continues to evolve, the United States finds itself at the forefront of emerging cybersecurity challenges. With its c...

Top 10 Dark Web Markets
Top 10 Dark Web Markets The dark web hosts markets like the internet’s Wild West. Sites like Silk Road and Nemesis have shown how deep this underworld goes. The shutdown of these platforms is a big wi...

The Anatomy of Stealers: How Are They Stealing Our Information? Where ...
The Anatomy of Stealers: How Are They Stealing Our Information? Where Are They Taking It? The world of cyber security faces new and more complex threats every day. Among these threats, which we encoun...
Power of AI: Dark Web Monitoring with ChatGPT
Power of AI: Dark Web Monitoring with ChatGPT The dark web, often shrouded in mystery and intrigue, is a part of the internet that remains hidden from conventional search engines and browsers. It̵...
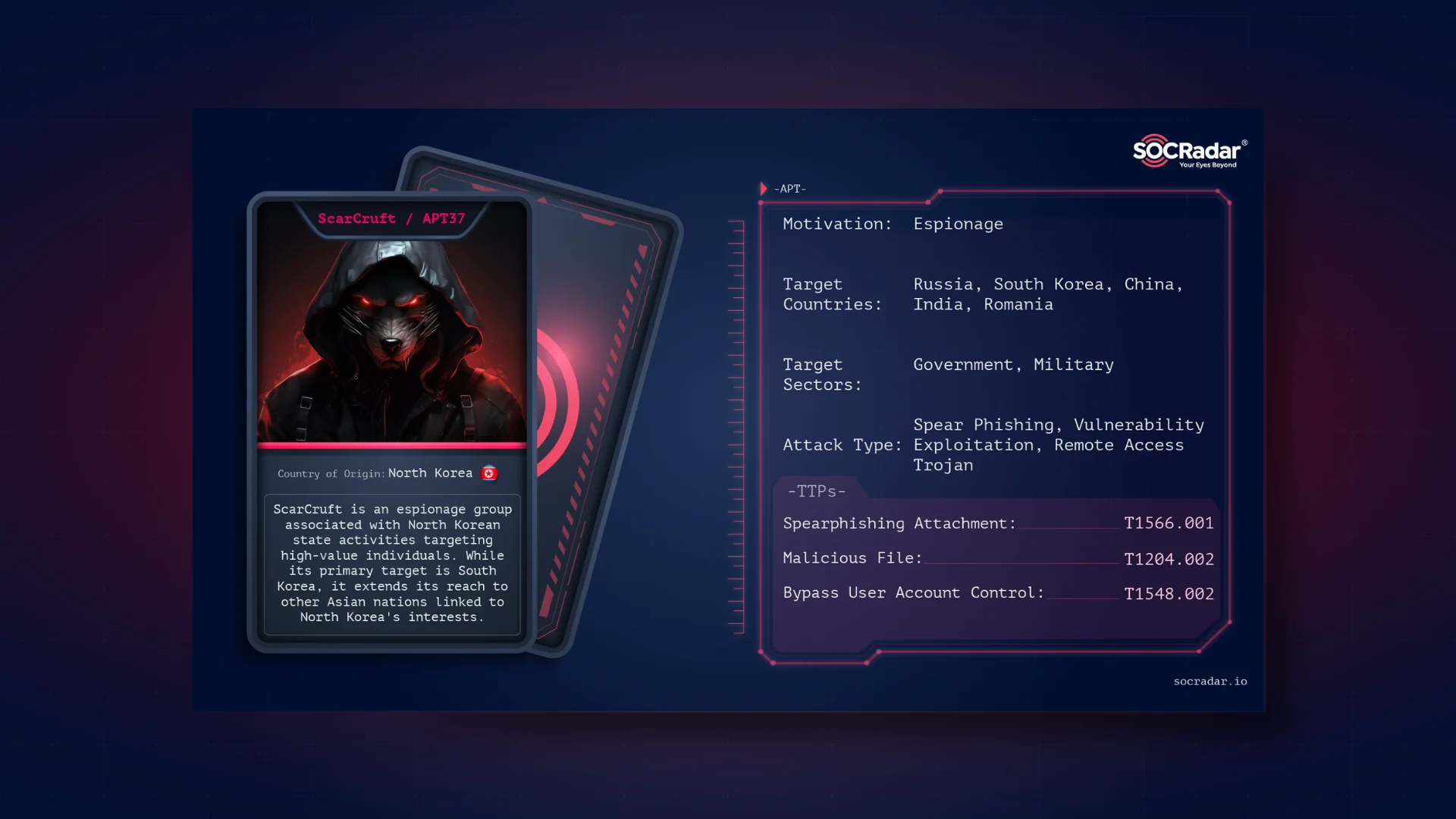
Threat Actor Profile: ScarCruft / APT37
Threat Actor Profile: ScarCruft / APT37 ScarCruft, also widely known as APT37 or Reaper APT, is an espionage group associated with North Korean state activities that target high-value individuals. The...

How to Combat Fraud with Threat Intelligence: Cutting-Edge Pathway
How to Combat Fraud with Threat Intelligence: Cutting-Edge Pathway Organizations have increasingly moved significant portions of their operations online to streamline customer service processes. Inste...

Cybersecurity Predictions: What Trends Will Be Prevalent in 2024?
Cybersecurity Predictions: What Trends Will Be Prevalent in 2024? The evolving digital environment and expanding attack surface demand vigilant adaptation to stay one step ahead of adversaries. Recogn...

Russian APT Operation: Star Blizzard
Russian APT Operation: Star Blizzard [Update] January 30, 2024: “Official Attributions of Star Blizzard” Within the continuously changing cyber threat landscape, the strategies of Star Blizzard unfold...

Writing YARA Rules with Custom GPTs and SOCRadar Platform
Writing YARA Rules with Custom GPTs and SOCRadar Platform YARA rules stand out as essential instruments for identifying and classifying malware. These rules are indispensable for cybersecurity profess...

Okta Customer Support System Breach: Lessons in Supply Chain Risks and...
Okta Customer Support System Breach: Lessons in Supply Chain Risks and Cybersecurity How successful are you in ensuring your cybersecurity in the digital environment? Personal and corporate data secur...

Dark Web Profile: Scattered Spider
Dark Web Profile: Scattered Spider [Update] July 17, 2024: “Collaboration with Qilin Ransomware” One hacker collective continues to confound federal law enforcement and cybersecurity experts — the Sca...

Dark Web Profile: Cyber Av3ngers
Dark Web Profile: Cyber Av3ngers The Cyber Av3ngers, reportedly connected to Iran’s Islamic Revolutionary Guard Corps, have become known for attacking critical infrastructure, especially in the ...

Overview of the Internet as an Attack Vector: Censys State of The Inte...
Overview of the Internet as an Attack Vector: Censys State of The Internet Report The Internet is a vast network that has revolutionized our daily lives. It encompasses many technologies, including we...

CISA Issues ICS Advisories on Mitsubishi, Delta, Franklin Electric, BD...
CISA Issues ICS Advisories on Mitsubishi, Delta, Franklin Electric, BD & Unitronics PLCs’ Active Exploitation The U.S. Cybersecurity and Infrastructure Security Agency (CISA) has recently issued ...

Exploitation Attempts Observed for Critical ownCloud Vulnerability (CV...
Exploitation Attempts Observed for Critical ownCloud Vulnerability (CVE-2023-49103) Exploitation activity targeting ownCloud with the CVE-2023-49103 vulnerability has been observed, raising concerns w...

MGM Casino Hack and Realities of Social Engineering Attacks
MGM Casino Hack and Realities of Social Engineering Attacks In the complicated world of cybersecurity, the most unpredictable element remains the human factor. Social engineering attacks exploit this ...
Cyber Awakeness Month: Takedown of Trigona, Hive Ransomware Resurges, ...
Cyber Awakeness Month: Takedown of Trigona, Hive Ransomware Resurges, RansomedForum and New RaaS ‘qBit’ From the takedown of Trigona to the resurgence of Hive Ransomware, and the emergence of a new ha...

Zero-Day Vulnerabilities in Citrix NetScaler and WinRAR Are Under Acti...
Zero-Day Vulnerabilities in Citrix NetScaler and WinRAR Are Under Active Exploitation (CVE-2023-4966, CVE-2023-38831) Serious vulnerabilities in Citrix NetScaler and WinRAR are currently being exploit...

VBScript Is Retiring: From Scripting to Security Threats
VBScript Is Retiring: From Scripting to Security Threats VBScript is facing retirement as Windows moves forward. In future Windows releases, VBScript will be offered as a feature on demand before its ...

MGM Resorts Hacked by BlackCat Affiliate, ‘Scattered Spider’
MGM Resorts Hacked by BlackCat Affiliate, ‘Scattered Spider’ A cybercriminal gang employing a combination of impersonation and malware is the prime suspect behind the cyberattack that crippled the ope...

Cyber Threat Intelligence (CTI) Roles for Ransomware Protection
Cyber Threat Intelligence (CTI) Roles for Ransomware Protection Ransomware attacks remain one of the most significant cyber threats against organizations today. Despite numerous countries launching co...




































