
Windows SmartScreen Vulnerability Exploited in DarkGate Malware Attack...
Windows SmartScreen Vulnerability Exploited in DarkGate Malware Attacks, Patch CVE-2024-21412 Now [Update] July 25, 2024: “Information Stealer Campaign Exploits the Windows SmartScreen Vulnerabi...
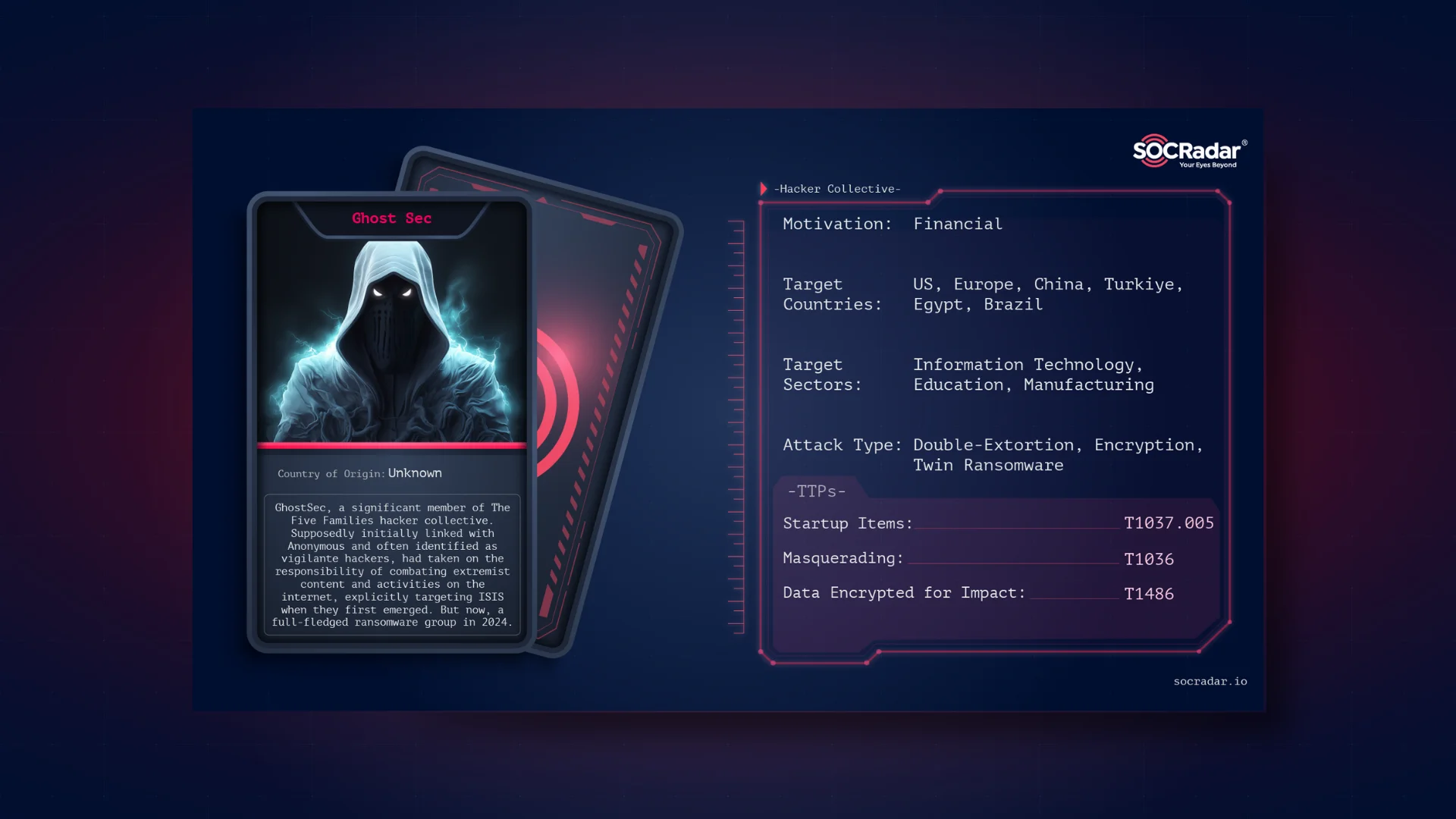
Dark Web Profile: GhostSec
Dark Web Profile: GhostSec [Update] May 16, 2024: “GhostSec Shifts Focus from Cybercrime to Hacktivism” GhostSec, a significant member of The Five Families, has garnered substantial attention with the...

Top 10 Training Platforms for SOC Analysts
Top 10 SOC Analysts Training Platforms Security Operations Center (SOC) analysts play an important role in defending against cyber threats. To meet the demands of this critical profession, aspiring an...

CISA Highlights Updates Addressing Adobe, Fortinet Vulnerabilities: CV...
CISA Highlights Updates Addressing Adobe, Fortinet Vulnerabilities: CVE-2023-42789, CVE-2023-48788, CVE-2024-20756, CVE-2024-20767 [Update] December 17, 2024: “CISA Adds CVE-2024-20767 to Known Exploi...
An Overview of Microsoft March 2024 Patch Tuesday: Severe RCE and Priv...
An Overview of Microsoft March 2024 Patch Tuesday: Severe RCE and Privilege Escalation Vulnerabilities Microsoft has released Patch Tuesday for March 2024, which addresses 61 security vulnerabilities....

Top 10 Vulnerabilities on the Dark Web in 2023
Top 10 Vulnerabilities on the Dark Web in 2023 In the Dark Web, where cybercriminals and hackers converge to trade secrets and illicit goods, vulnerabilities can easily become weapons for many, and th...

Dark Web Profile: Meow Ransomware
Dark Web Profile: Meow Ransomware In late 2022, 4 ransomware strains were discovered that are derived from Conti‘s leaked ransomware strain. One of them was Meow ransomware. The operation of this cryp...

Critical CVE-2024-21899 Vulnerability in QNAP Products; Upcoming PoC E...
Critical CVE-2024-21899 Vulnerability in QNAP Products; Upcoming PoC Exploit for Outlook Vulnerability, CVE-2024-21378 QNAP recently addressed three vulnerabilities affecting their QTS, QuTS hero, QuT...

Acuity Federal Contractor Breach, Okta Customers Leak, DCRat Exploit a...
Acuity Federal Contractor Breach, Okta Customers Leak, DCRat Exploit and Access Sales In the Dark Web, a world of illicit activities and cyber threats, the SOCRadar Dark Web Team has uncovered a serie...

Operational Technology (OT) and Cybersecurity: Safeguarding Critical I...
Operational Technology (OT) and Cybersecurity: Safeguarding Critical Infrastructure Operational Technology (OT) encompasses hardware and software capable of detecting or inducing alterations in indust...

Top 5 Paste Sites Used by Threat Actors
Top 5 Paste Sites Used by Threat Actors Paste sites are increasingly being utilized as hubs for disseminating code snippets, configuration files, and assorted textual data. While they offer valuable r...

Critical Veritas NetBackup & JFrog Artifactory Vulnerabilities (CVE-20...
Critical Veritas NetBackup & JFrog Artifactory Vulnerabilities (CVE-2024-28222, CVE-2023-42662); CISA Alert for Cisco Flaws New critical vulnerabilities have surfaced in Veritas NetBackup and JFro...

The Dangers of Third-Party App Stores: Risks and Precautions
The Dangers of Third-Party App Stores: Risks and Precautions When downloading applications, smartphone users typically consider the pre-installed Apple App Store or Google Play. However, there are oth...

Dark Peep #12: The Ransomware Group That Never Was
Dark Peep #12: The Ransomware Group That Never Was Welcome to Dark Peep #12, where we dive into the latest cyber escapades reminiscent of tales from the Wild West. This edition is packed with stories ...
How to Leverage Threat Intelligence in Incident Response
How to Leverage Threat Intelligence in Incident Response In the ever-evolving landscape of cybersecurity threats, incident response has become a crucial component of any organization’s defense s...

Navigating the Shadowy Depths of the Migo Malware Campaign
Navigating the Shadowy Depths of the Migo Malware Campaign The Migo malware campaign emerged as a formidable adversary, targeting Redis servers with novel system-weakening techniques aimed at cryptoja...

VMware ESXi, Workstation, Fusion Vulnerabilities Allow Code Execution,...
VMware ESXi, Workstation, Fusion Vulnerabilities Allow Code Execution, Sandbox Escape (CVE-2024-22252 – 22255) [Update] March 7, 2024: “CISA Urges Swift Patching of VMware Vulnerabilities” VMware has ...

ALPHV's Roller Coaster, $22 Million Ransom
ALPHV’s Roller Coaster, $22 Million Ransom [Update] March 7, 2024: “Money Paid, Data Retained; ALPHV’s Exit Scam” The ransomware attack on Change Healthcare has become one of the most disruptive...

TeamCity On-Premises Vulnerabilities Threaten Supply Chains (CVE-2024-...
TeamCity On-Premises Vulnerabilities Threaten Supply Chains (CVE-2024-27198, CVE-2024-27199); Android March 2024 Updates [Update] March 12, 2024: “BianLian Exploits JetBrains TeamCity Vulnerabilities ...

Defending the Inbox: Vulnerabilities of Secure Email Gateways
Defending the Inbox: Vulnerabilities of Secure Email Gateways In an era where digital communication reigns supreme, email remains a cornerstone of modern business and personal correspondence. However,...
































