
IcedID Macro Attacks Deploy Nokoyawa Ransomware
IcedID Macro Attacks Deploy Nokoyawa Ransomware Malicious actors frequently resort to alternative techniques to gain initial access, such as employing diverse file formats and payloads. It is importan...

Credit Card, RDP Access, Health, and Business Data Sales
Credit Card, RDP Access, Health, and Business Data Sales Welcome to this week’s edition of our dark web news summary, where we bring you the latest updates on the clandestine world of cybercrime...

G7: Cybersecurity Reflections
G7: Cybersecurity Reflections The G7 Cybersecurity Summit 2023 is just around the corner and is being held in Hiroshima, Japan, which is a city that was devastated by an atomic bomb attack in 1945, no...
Unlock Industry-Specific Cyber Insights: Industry Threat Landscape Rep...
Unlock Industry-Specific Cyber Insights: Industry Threat Landscape Report Industry cyber threat landscape means the perspective of distinct cybersecurity threats targeting the related industry. The th...

Vulnerability in KeePass Password Manager Permits Retrieving Master Pa...
Vulnerability in KeePass Password Manager Permits Retrieving Master Password (CVE-2023-32784) [Update] June 6, 2023: KeePass has fixed the CVE-2023-32784 vulnerability in version 2.54. Attacks leverag...

Network Devices Under Threat: Mustang Panda Targets TP-Link Routers, C...
Network Devices Under Threat: Mustang Panda Targets TP-Link Routers, Critical Teltonika Vulnerabilities The attacks targeting European foreign affairs entities since January 2023 have been attributed...

Major Cyberattacks in Review: April 2023
Major Cyberattacks in Review: April 2023 In April 2023, several cybersecurity incidents were reported across various industries. These included supply chain attacks, data breaches, and cryptocurrency ...

5 Lessons Learned from Healthcare Industry Cyberattacks in 2022
5 Lessons Learned from Healthcare Industry Cyberattacks in 2022 Like other critical infrastructures, the healthcare industry is frequently targeted by cyberattacks. The attacks in the healthcare verti...

VMware Vulnerability Exploit, Invicta Stealer, and Source Code Sales
VMware Vulnerability Exploit, Invicta Stealer, and Source Code Sales This week’s headlines feature some developments that highlight the ongoing threats posed by cybercriminals. First up, we have...

Recent Data Breaches: Capita, Toyota, and Discord
Recent Data Breaches: Capita, Toyota, and Discord [Update] June 6, 2023: Capita was previously unable to confirm whether hackers had exfiltrated any data. Some USS (Universities Superannuation Scheme...

Gulf Countries Threat Landscape Report: Cyber Security Posture of the ...
Gulf Countries Threat Landscape Report: Cyber Security Posture of the GCC Countries “Bahrain, Kuwait, Oman, Qatar, Saudi Arabia, and the United Arab Emirates constitute the Cooperation Council for the...

Essential Addons for Elementor WordPress Plugin Allows Privilege Escal...
Essential Addons for Elementor WordPress Plugin Allows Privilege Escalation (CVE-2023-32243) A popular WordPress plugin called Essential Addons for Elementor has a security vulnerability, tracked as C...

Cyber Deception at the Ballot Box: Unmasking the Phishing Epidemic in ...
Cyber Deception at the Ballot Box: Unmasking the Phishing Epidemic in Election Campaigns During periods of elections, people’s desire to obtain knowledge is outstanding, and they are overloaded ...

Scammers Distribute Malware via Verified Account Ads on Facebook
Scammers Distribute Malware via Verified Account Ads on Facebook Scamming campaigns frequently involve threat actors impersonating businesses or significant individuals. However, a recent trend of Fac...

Increased Healthcare Security Breaches in 2022
Increased Healthcare Security Breaches in 2022 Data from the US government shows that there has been a significant increase in healthcare security breaches. At least 125 data breaches of healthcare o...

Microsoft's May 2023 Patch Tuesday Addresses Three Zero-Day Vulnerabil...
Microsoft’s May 2023 Patch Tuesday Addresses Three Zero-Day Vulnerabilities Microsoft has released the May 2023 Patch Tuesday update and it addresses 40 security vulnerabilities. The patch addre...

Ever-Changing Tactics on Social Engineering
Ever-Changing Tactics on Social Engineering In today’s digital age, cyber threats are becoming increasingly common, and one of the most prevalent types of attacks is phishing. Phishing involves ...
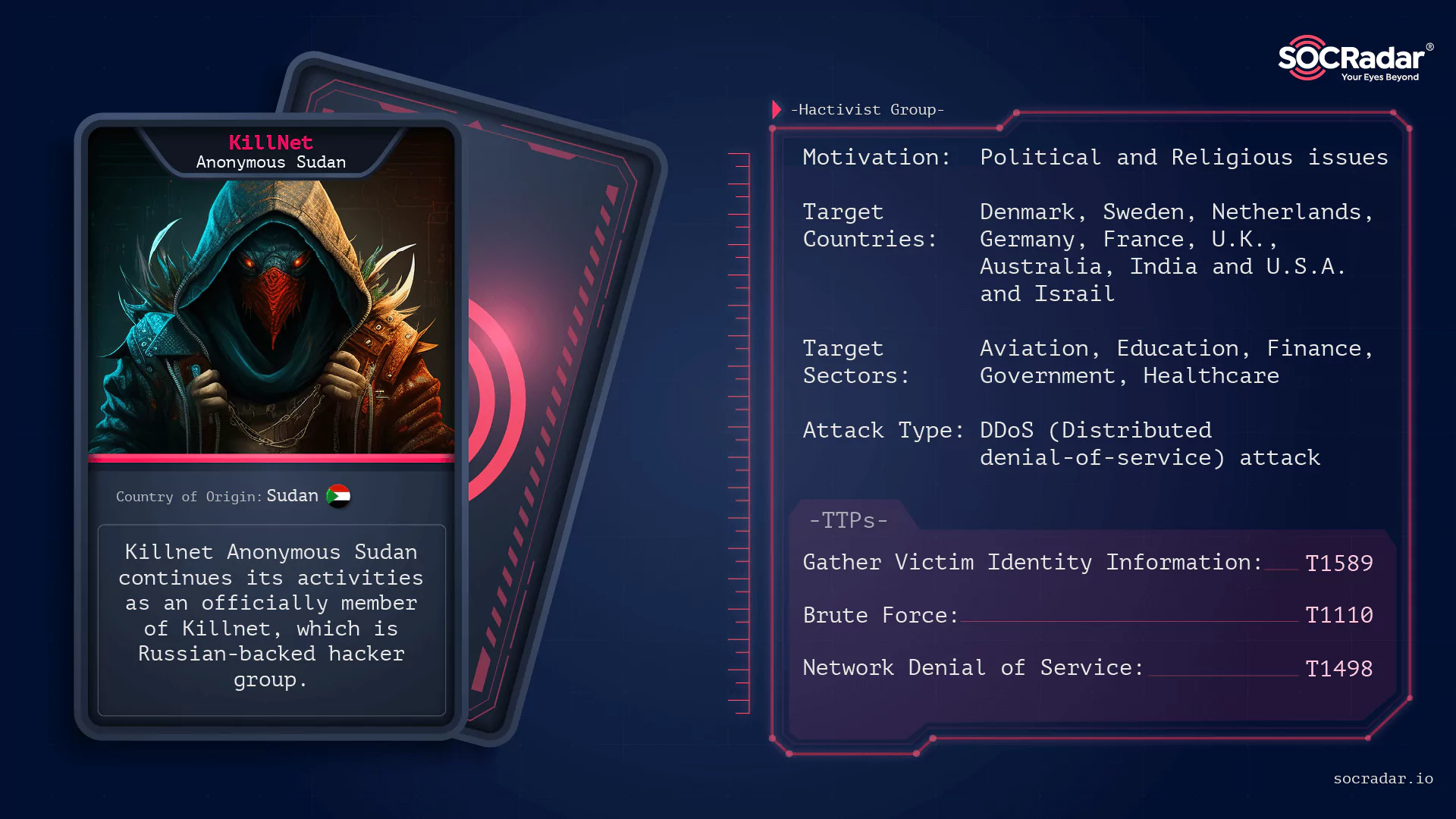
Dark Web Profile: KillNet Anonymous Sudan
Dark Web Profile: KillNet Anonymous Sudan [Update] October 17, 2024: “Indictment of Two Sudanese Nationals Behind Anonymous Sudan” [Update] July 5, 2023: In a recent cyber attack, Anonymous Sudan clai...

Money Message Ransomware Leaks MSI Signing Keys for Intel Boot Guard
Money Message Ransomware Leaks MSI Signing Keys for Intel Boot Guard MSI, a leading Taiwanese PC manufacturer, suffered a ransomware attack last month. The threat actors behind the...

Vocalcom Ransomware Attack, Credit Card Sales, and Botnet Services
Vocalcom Ransomware Attack, Credit Card Sales, and Botnet Services This week, we have some troubling news to share, like always. We’ve learned that half a million credit cards belonging to Brazi...

































